Cyber threats remain costly, with IBM reporting an average breach of $4.44M. As cloud-native stacks widen the attack surface, enterprises are adopting continuous security monitoring to detect anomalies in real time and contain threats faster.
This is where CubeAPM stands apart. It delivers real-time anomaly detection that highlights threats like suspicious API activity, error surges, or latency spikes. With governance tools such as RBAC, SSO, and audit logging, CubeAPM helps enterprises catch intrusions early, cut response times, and secure both apps and infrastructure.
In this article, we’ll cover the Top Security Monitoring Tools, comparing CubeAPM with Datadog, New Relic, Dynatrace, and others, giving you a clear framework to choose the right solution for scale, compliance, and budget.
Top 8 Security Monitoring Tools
- CubeAPM
- Datadog
- New Relic
- Dynatrace
- Sumo Logic
- Microsoft Sentinel
- Splunk AppDynamics(Enterprise Security)
- Elastic Observability Security
How Observability Data (Logs, Traces, Metrics) Helps Security Teams Investigate Incidents
Logs, traces, and metrics together are essential for modern security monitoring. Logs remain essential for recording discrete events such as failed logins, API calls, or configuration changes that point directly to suspicious activity. But on their own, logs can generate overwhelming volumes of alerts, making it hard to separate noise from real threats.
This is where traces and metrics add critical context. Traces map the full path of a request across microservices, helping security teams uncover lateral movement, unusual dependencies, or hidden data flows during an attack. Metrics track patterns like sudden CPU spikes, abnormal latency, or network surges—early indicators that something is wrong at the infrastructure level.
Attacks often unfold across multiple layers—applications, APIs, containers, and infrastructure—making it difficult to connect the dots when relying on a single signal type. This is where observability data becomes critical for security teams.
- Logs capture discrete events like failed logins, unusual API requests, or configuration changes. Security analysts can use them to trace suspicious activities back to specific users, services, or endpoints.
- Traces reveal end-to-end request flows across microservices, exposing abnormal call chains, unauthorized lateral movement, or hidden data exfiltration paths.
- Metrics provide behavioral baselines—such as latency spikes, CPU surges, or unusual traffic patterns—that often serve as the first indicators of compromise.
When combined, these signals transform incident investigation. Instead of isolated alerts, teams can reconstruct attack timelines, validate whether a vulnerability was actively exploited, and prioritize responses based on real impact. This correlation not only shortens mean time to detect (MTTD) and respond (MTTR) but also reduces alert fatigue, giving analysts confidence that they’re acting on the right threats.
In short, observability data doesn’t just monitor system health—it acts as a forensic backbone for security monitoring, helping enterprises contain breaches faster and with greater accuracy.
What is a Security Monitoring Tool?

A security monitoring tool is software designed to detect, analyze, and respond to threats across applications, infrastructure, and networks in real time. Unlike traditional SIEMs that focus mainly on log collection, modern security monitoring platforms unify metrics, logs, traces, and events to give security teams full visibility into suspicious activity. They help spot anomalies like failed login spikes, unusual API calls, container restarts, or privilege escalations.
At its core, security monitoring tools help organizations:
- Detect threats early by correlating anomalies like failed logins, unusual traffic, or code injections.
- Investigate faster with root-cause analysis across applications, infrastructure, and endpoints.
- Enforce compliance for frameworks like GDPR, HIPAA, PCI DSS, and DPDP, where audit trails and data localization are mandatory.
- Reduce breach impact by shortening Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR).
This practice has evolved into Continuous Security Monitoring (CSM), where monitoring isn’t just about alerting—it’s about proactively hardening infrastructure, enforcing security posture, and automating response actions.
Yet despite these advances, challenges remain: high data ingestion costs, lack of transparency in pricing, and scalability issues in legacy SIEMs make it difficult for teams to monitor effectively without budget overruns.
Key Features to Look for in a Security Monitoring Tool
1. Real-time, multi-signal correlation (logs, metrics, traces, events)
Security monitoring is no longer effective when signals are siloed. The best tools fuse logs, metrics, traces, and events into a single timeline to uncover attack patterns as they unfold. For example, a suspicious login event can be correlated with distributed tracing data to show lateral movement inside microservices, while infrastructure monitoring reveals if abnormal CPU or network activity is tied to the incident.
2. Risk-based alerting (RBA)
Traditional security tools flood teams with alerts, making it hard to prioritize. Risk-based alerting (RBA) solves this by scoring alerts based on severity, exploitability, and user or entity behavior analytics. Combined with uptime monitoring and distributed tracing, RBA can highlight whether a risky behavior—like credential stuffing—caused downtime or performance issues across services.
3. Runtime application security
Static scans catch vulnerabilities in code, but modern attacks exploit gaps at runtime. A strong security monitoring tool must offer runtime application security to analyze vulnerabilities in production, confirming whether they are exploitable. By linking runtime detections with logs, traces, and infrastructure monitoring, security teams can prioritize based on real-world impact, not just potential risk. This ensures that remediation targets the vulnerabilities that actually threaten uptime and customer data.
4. Detection engineering that scales
Threats evolve quickly, so detection rules must scale just as fast. Tools that enable Detection-as-Code let security teams version, test, and deploy rules with the same rigor as software. Scalable detection engineering should support threshold alerts, anomaly detection, impossible travel scenarios, and new-value detection. When integrated with enterprise monitoring, these rules don’t just trigger alerts—they give full context on where in the infrastructure the abnormal behavior originated, helping reduce investigation times.
5. Threat intelligence enrichment
Security monitoring is far more effective when events are enriched with external intelligence. First-class ingestion of indicators—such as IPs, file hashes, or malicious domains—lets teams correlate logs and metrics against known threats in real time. With enrichment tied into infrastructure monitoring and uptime tracking, teams can quickly see if a threat indicator correlates with degraded system performance or suspicious traffic patterns. This blending of external intel with internal telemetry strengthens defenses while cutting through noise.
Example: How CubeAPM Handles Security Monitoring
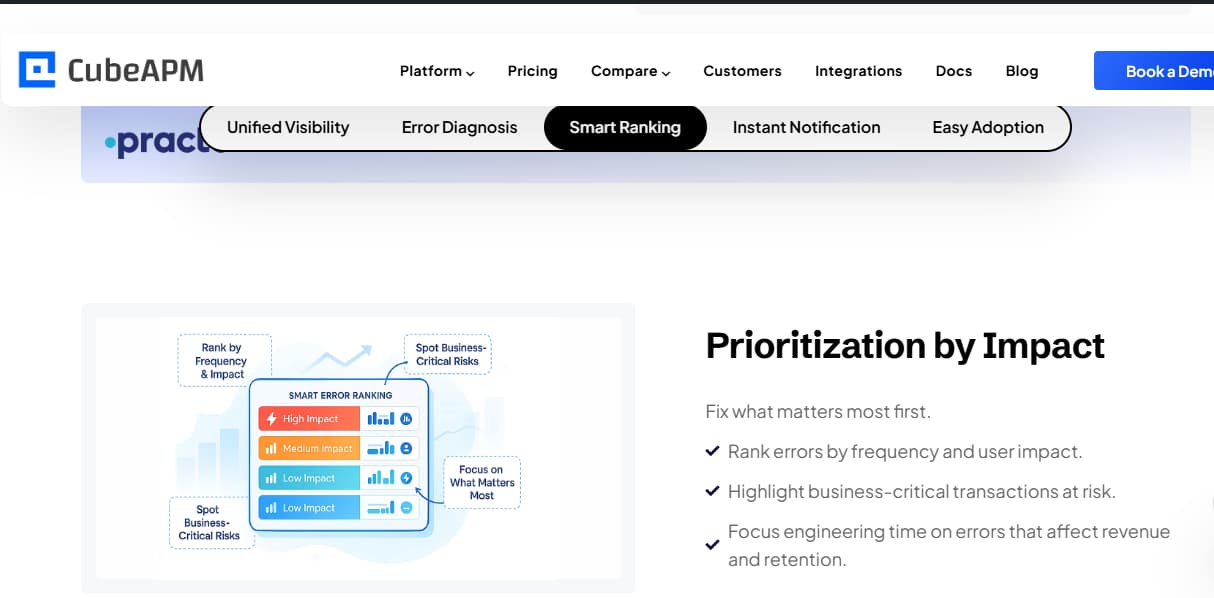
CubeAPM enhances observability by integrating basic security monitoring, transforming logs, traces, metrics, and events into actionable signals that highlight unusual or potentially risky behavior. Its smart sampling and correlation engine reduces noise and surfaces anomalies such as repeated failed logins, suspicious API traffic, or latency spikes that may suggest abuse or intrusion.
- Logs – Capture and correlate authentication attempts, API requests, and system changes to surface early indicators of compromise.
- Traces – Reveal unexpected service-to-service calls, unusual data flows, or lateral movement across microservices.
- Metrics – Expose infrastructure anomalies like traffic surges, container restarts, or resource spikes that may align with attack patterns.
Why Teams Choose Different Security Monitoring Tools
1. High Costs That Don’t Match Value
As data grows, platforms like Splunk or Datadog can become prohibitively expensive. Users often feel pricing doesn’t scale fairly with the value they get.
2. Excessive Noise and False Positives
Alert fatigue is a top frustration. Too many low-value or false alerts drown out genuine threats, wasting analyst time.
3. Speed and Human Collaboration
Many teams don’t just want alerts—they need fast detection and the ability to collaborate with the vendor’s SOC. Tools that act like a black box are less attractive.
4. Managing Multiple Tools vs. One Platform
Some teams are dissatisfied with paying for overlapping tools. They want flexibility without being locked into bloated “all-in-one” stacks.
5. Vendor Lock-In & Limited Flexibility
Traditional SIEMs force teams to use proprietary agents or licensing models. Migrating data out of these platforms is expensive and complex. More teams now prefer OpenTelemetry-native tools, which allow switching vendors without rewriting instrumentation.
Top 8 Security Monitoring Tools
1. CubeAPM

Known For
CubeAPM is an OpenTelemetry-native observability and security monitoring platform offering full MELT (Metrics, Events, Logs, Traces) coverage, compliance-friendly deployments, and transparent pricing that is 60–80% cheaper than traditional SaaS vendors.
Security Monitoring Features
- Anomaly Detection with Smart Sampling: Detects suspicious events like latency spikes, unusual errors, or traffic anomalies while filtering noise.
- On-Prem Hosting for Compliance: Stores all telemetry data inside your cloud or data center, supporting GDPR, HIPAA, and DPDP requirements.
- RBAC & Governance: Role-based access control, SSO, MFA, and audit logs for enterprise-grade governance.
- Secure Integrations: Compatible with OTEL, Prometheus, Datadog, and New Relic agents for vendor-neutral, secure data collection.
Key Features
- Unified MELT Stack: Correlates logs, metrics, traces, errors, and synthetics for end-to-end monitoring.
- Smart Sampling Engine: Retains critical telemetry, reducing cost.
- Unlimited Data Retention: No extra cost for storing historical telemetry.
- Rapid Support: Slack/WhatsApp access to core engineers with sub-5 min turnaround vs multi-day email tickets.
Pros
- Transparent pricing, no per-user or per-host fees.
- Up to 80% cheaper than Datadog/New Relic at scale.
- Strong compliance coverage with on-prem hosting.
- High compatibility (OTEL, Prometheus, Elastic, Datadog agents).
- Sub-5 min support SLAs.
Cons
- Not suited for teams looking for off-prem solutions
- Strictly an observability platform and does not support cloud security management
Best For
- Startups/SMBs needing predictable observability + security monitoring.
- Enterprises with high ingestion volumes (10TB+/month).
Pricing
- Flat pricing of 0.15/GB of data ingested
Cube APM Security Monitoring Pricing at Scale
*All pricing comparisons are calculated using standardized Small/Medium/Large team profiles defined in our internal benchmarking sheet, based on fixed log, metrics, trace, and retention assumptions. Actual pricing may vary by usage, region, and plan structure. Please confirm current pricing with each vendor.
For a mid-sized SaaS company ingesting 45TB(~45,000) total monthly data ingestion and 45,000TB of observability data outcharged by the cloud provider, the total cost will be about ~$7200/month.
Tech Fit
CubeAPM is best for teams modernizing around Kubernetes, serverless, or hybrid cloud that require cost control + compliance. Its OTEL-native architecture ensures vendor neutrality, while on-prem deployment options make it ideal for finance, healthcare, and government workloads with strict data sovereignty needs.
2. Datadog
Known For
Datadog is a cloud-first observability and security monitoring platform widely adopted for its vast ecosystem of 900+ integrations and ability to monitor almost any workload. It extends observability into security with Cloud SIEM, Threat Detection, and Compliance Monitoring capabilities.
Security Monitoring Features
- Cloud SIEM: Detects threats in real time with rules mapped to the MITRE ATT&CK framework.
- Compliance Monitoring: Continuously checks cloud environments for misconfigurations against frameworks like PCI DSS, HIPAA, and SOC 2.
- Workload Security: Protects containers, VMs, and Kubernetes workloads with runtime monitoring.
- Identity Monitoring: Detects anomalous login attempts and permission escalations.
Key Features
- Full-Stack Observability: Metrics, traces, logs, RUM, synthetics, and infra in one platform.
- Threat Detection Rules: 900+ built-in detection rules with anomaly correlation.
- SIEM + Observability: Integrates log analytics with security monitoring to reduce investigation time.
- Extensive Integrations: 900+ native connectors across AWS, GCP, Azure, Kubernetes, and SaaS.
Pros
- Broadest coverage of modern stacks and cloud-native workloads.
- Real-time security alerts tied to MITRE ATT&CK.
- Unified dashboards for observability + security.
- Mature ecosystem with wide enterprise adoption.
Cons
- Expensive at scale with ingestion-based billing.
- Costs spread across multiple products (APM, logs, SIEM, compliance).
- Steep learning curve for newcomers.
Pricing
- APM (Pro Plan): $35/host/month
- Infra (Pro Plan): $15/host/month
- Ingested Logs: $0.10 per ingested or scanned GB per month
Datadog Security Monitoring Pricing at Scale
For a mid-sized SaaS company operating 125 APM hosts, 40 profiled hosts, 100 profiled container hosts, 500,000,000 indexed spans, 200 infra hosts, 1,500,000 container hours, 300,000 custom metrics, and ingesting around 10TB(~10,000 GB) of logs per month with 3500 indexed logs, the monthly cost would be around ~$27,475/month.
Tech Fit
Datadog fits large enterprises or fast-scaling SaaS teams that need all-in-one observability + security monitoring and can absorb higher costs. Its cloud-first design and breadth of integrations make it strong for Kubernetes, multi-cloud, and hybrid IT environments.
3. New Relic
Known For
New Relic is a pioneer in application performance and observability, now extended with security monitoring capabilities. It is popular for its developer-friendly agents, deep JVM monitoring, and strong adoption among engineering teams modernizing monoliths and microservices.
Security Monitoring Features
- Vulnerability Management: Detects insecure libraries and dependencies across applications.
- Logs in Context: Correlates security-related log events with traces and metrics for faster root cause analysis.
- Error & Anomaly Tracking: Surfaces spikes in error rates and unusual behaviors that may indicate threats.
- Data Compliance: Retention requires extra fees, with telemetry stored on New Relic servers outside customer regions.
Key Features
- Full-Stack Monitoring: Application, infrastructure, mobile, browser, logs, and synthetics.
- Granular APM Tracing: Strong JVM and backend observability with transaction-level detail.
- AI/ML Insights: Automated anomaly detection and alerting for suspicious activity.
- Wide Language Support: Agents for Java, .NET, Node.js, Python, Ruby, and more.
Pros
- Easy onboarding with developer-friendly agents.
- Strong tracing depth for backend and JVM-heavy environments.
- Unified dashboards for infra + app monitoring.
- Strong ecosystem and integrations.
Cons
- High costs at scale due to ingestion-based billing.
- Learning curve for non-developers due to scripting-heavy monitors
Pricing
- Free Tier: 100GB/month ingested
- Pro plan: $0.40/GB ingested beyond the free 100GB limit
- Pro Plan: $349/user for full platform user
New Relic Security Monitoring Pricing at Scale
A mid-sized SaaS company ingesting 45TB (~45,000 GB) of telemetry data per month and with 10 full users, the cost would come around ~$25,990/month.
Tech Fit
New Relic works best for engineering teams needing deep application visibility—especially JVM-heavy stacks. It’s attractive for organizations that want fast onboarding and rich tracing.
4. Dynatrace
Known For
Dynatrace is an enterprise-grade observability and security monitoring platform used heavily by Fortune 500 companies. It’s recognized for its AI-powered Davis engine, which automates anomaly detection, root-cause analysis, and even remediation.
Security Monitoring Features
- Application Security Module: Identifies vulnerabilities in runtime environments, frameworks, and third-party libraries.
- Runtime Threat Detection: Monitors Kubernetes, containers, and VMs for exploits, misconfigurations, or suspicious activity.
- Compliance Monitoring: Tracks cloud misconfigurations and provides reports for SOC 2, GDPR, HIPAA, and other frameworks.
- AI-Powered Risk Prioritization: Uses Davis AI to rank vulnerabilities by potential business impact.
Key Features
- Full-Stack Observability: Infrastructure, APM, logs, synthetics, RUM, and security in one platform.
- End-to-End Tracing: Granular service and transaction monitoring across distributed systems.
- Cloud-Native Support: Deep integrations with Kubernetes, OpenShift, AWS, Azure, and GCP.
- Davis AI Engine: Automates anomaly detection, RCA, and predictive analytics.
Pros
- Strong AI-driven automation for anomaly detection and RCA.
- Broad integrations across cloud and hybrid environments.
- Deep Kubernetes and container monitoring.
- Unified observability + security workflows.
Cons
- Expensive as costs scale.
- Steeper learning curve for small teams.
Pricing
- Infrastructure Monitoring: $29 / mo per host
- Full-Stack Monitoring: $58 / mo per 8 GiB host
Dynatrace Security Monitoring Pricing at Scale
A midsized SaaS company operating 125 APM hosts, 200 infra hosts, 10TB(~10,000 GB) of ingested logs, 300,000 custom metrics, 1,500,000 container hours, and 45,000GB of observability data out(charged by cloud provider), the cost would come around ~$21,850/month.
Tech Fit
Dynatrace is best suited for large enterprises and regulated industries with complex, hybrid, or multi-cloud deployments. Its AI-driven automation reduces analyst overhead, but the cost and complexity often make it less attractive for SMBs or cost-sensitive SaaS companies.
5. Sumo Logic
Known For
Sumo Logic is a cloud-native log management and security analytics platform that combines observability with SIEM capabilities. It’s often chosen by teams looking for flexible data analytics, real-time dashboards, and continuous security monitoring in SaaS environments.
Security Monitoring Features
- Cloud SIEM: Detects and correlates threats across logs, metrics, and events in real time.
- Cloud Security Analytics: Provides anomaly detection and threat hunting across multi-cloud and SaaS applications.
- Compliance Reporting: Built-in dashboards for PCI, HIPAA, GDPR, and SOC 2 compliance checks.
- Threat Intelligence Feeds: Enriches logs with third-party intelligence to identify known malicious IPs or domains.
Key Features
- Log Management at Scale: Centralized ingestion, indexing, and querying of massive log volumes.
- Anomaly Detection: ML-based correlation rules to surface suspicious behaviors.
- Observability + Security: Metrics, traces, and logs unified in one SaaS platform.
- Flexible Dashboards: Highly customizable visualizations for security and ops teams.
Pros
- Strong SIEM capabilities built directly into log analytics.
- Flexible and customizable dashboards.
- Native integrations with AWS, Azure, GCP, and SaaS platforms.
- Good compliance reporting out-of-the-box.
Cons
- Pricing can escalate quickly with high log ingestion.
- Query language can be steep for new users.
Pricing
- Free tier + enterprise plans. Pricing is based on data ingest and features enabled.
- Logs: $2.50/GB (standard ingest)
- Metrics: available via add-ons
- Traces: supported but priced as part of advanced observability plans
Sumo Logic Security Monitoring Pricing at Scale
For a midsized SaaS ingesting 45TB(~45,000GB) of logs per month and 45,000GB of observability data out(charged by cloud provider), the cost would come around ~$16,065/month.
Tech Fit
Sumo Logic works best for cloud-native teams that need a single SaaS platform for both observability and security analytics. It’s strong for multi-cloud monitoring and compliance reporting, but SaaS-only hosting and pricing at scale can be limiting for regulated industries.
6. Microsoft Sentinel
Known For
Microsoft Sentinel is a cloud-native SIEM and SOAR platform built into the Azure ecosystem. It’s widely used by enterprises already invested in Microsoft services, offering deep integrations with Azure AD, Office 365, and Microsoft Defender.
Security Monitoring Features
- Cloud-Native SIEM: Collects and correlates security data from across on-prem and multi-cloud environments.
- Automated SOAR Playbooks: Uses Azure Logic Apps to automatically respond to incidents (e.g., disable compromised accounts).
- Threat Intelligence Integration: Enriches logs with Microsoft threat intelligence feeds for advanced correlation.
- Compliance & Governance: Pre-built templates for standards like HIPAA, GDPR, PCI DSS, and FedRAMP.
Key Features
- Log Analytics at Scale: Built on Azure Log Analytics for handling petabytes of data.
- AI-Powered Detection: Uses Microsoft’s ML models to reduce false positives.
- Multi-Cloud & Hybrid Support: Integrates with AWS, GCP, and on-prem security tools.
- Visualization: Dashboards in Azure Portal and Power BI integration.
Pros
- Deep integration with the Microsoft ecosystem.
- Powerful automation through SOAR playbooks.
- Scales easily for large enterprises.
- Strong compliance coverage.
Cons
- Pricing complexity: billed on data ingestion + retention.
- Can get expensive for high log volumes.
- Requires Azure expertise to configure effectively.
Pricing
- Data lake ingestion: $0.05/GB processed
- Data lake storage: $0.026/GB/month stored
- Data lake query: $0.005/GB analyzed
- Advanced Data Insights: $0.15 per compute hour
Microsoft Sentinel Security Monitoring Pricing at Scale
For a midsized SaaS company operating 50 hosts and ingesting 10TB of logs per month with 90-day retention, Sentinel’s costs add up fast. Data ingestion alone totals $500/month (10,000 GB × $0.05), while storage for 30TB across 3 months adds another $780/month (30,000 GB × $0.026). Running queries on all ingested data contributes $50/month (10,000 GB × $0.005), and assuming 200 compute hours for advanced analytics adds $30/month (200 × $0.15). Altogether, the monthly bill comes to roughly $1,360/month, excluding any Azure infrastructure costs, showing how Sentinel scales as more data and queries are added.
Tech Fit
Microsoft Sentinel is best suited for enterprises deeply embedded in the Microsoft/Azure ecosystem that want SIEM + SOAR in a single pane. It’s powerful for compliance-heavy industries, but high ingestion costs make it less attractive for log-heavy workloads outside Microsoft’s cloud.
7. Splunk AppDynamics (Enterprise Security)
Known For
A widely adopted, analytics-driven SIEM platform used by enterprises for threat detection, investigation, and response—offered both on-prem and in the cloud.
Security Monitoring Features
- Real-time threat detection using customizable correlation searches and Machine Learning via UBA integration.
- Investigation Workbench & Incident Review Dashboards for streamlined triage and root-cause analysis.
- Use Case Library and Event Sequencing to detect and group related threat events quickly.
- Flexible deployment with on-prem/cloud options and support for SOAR orchestration via Splunk SOAR.
Key Features
- Customizable security posture dashboards and Risk Analysis views.
- Integration with Threat Intelligence feeds and adaptive response mechanisms.
- High scalability—handles terabytes per day, supports large deployments.
Pros
- Rich analytics and enterprise-grade SIEM capabilities.
- Highly customizable dashboards and strong investigation workflows.
- Integrates across the broader Splunk ecosystem (SOAR, UBA, ML).
Cons
- Pricing is opaque; you must contact sales for quotes.
- Cost structure based on daily data ingestion, compute units, or number of monitored entities—complex to estimate.
- Expensive at scale and often overkill for smaller teams.
Pricing
- AppDynamics APM: starts at $33/month/CPU core
- Infra Monitoring: starts at $6/month/CPU core
Splunk AppDynamics Security Monitoring Pricing at Scale
For a mid-sized SaaS company running 125 hosts and 45,000GB of observability data out(charged by cloud provider), the cost will be around ~$8,625/month.
Tech Fit
Suited for large enterprises or MSSPs with mature SOC teams needing deep SIEM capabilities, custom logic, and integration with Splunk’s broader security ecosystem—but cost and complexity can be significant hurdles for smaller or regulated organizations.
8. Elastic Observability Security
Known For
A modern, usage-based SIEM and security analytics platform, part of the Elastic Cloud Serverless offering—designed for scalable, fast deployment with AI-infused workflows.
Security Monitoring Features
- Prebuilt detection rules, threat hunting, and collaboration workflows.
- Entity analytics (UEBA) and AI-assisted hunting with Elastic’s AI Assistant.
- Optional Endpoint Protection for malware/ransomware defence and Cloud Protection (CSPM, workload runtime defence).
Key Features
- Serverless, plug-and-play deployment with pay-per-use pricing.
- Rich detection and hunting capabilities with generative-AI enhancements.
- Optional asset-based protection for endpoints and cloud workloads.
Pros
- Transparent usage-based pricing with fast onboarding.
- AI-driven analytics and flexible deployment (no infra overhead).
- Endpoint and cloud posture protection is modular and optional.
Cons
- More expensive ingestion rates compared to some peers.
- Storage and infra costs grow rapidly.
- Requires in-house expertise to tune.
Pricing
- Standard: $99/month
- Gold: $114/month
- Platinum: $131/month
- Enterprise: $184/month
Elastic Enterprise Security Monitoring Pricing at Scale
For a mid-sized SaaS company with 125 APM hosts, 20TB of events ingestion per month, and 45,000GB of observability data out(charged by cloud provider), the cost would be around $17,435.
Tech Fit
A strong match for organizations needing fast setup, AI-rich security analytics, and modular protection. Great for cloud-native teams that embrace serverless infrastructure—but cost can escalate with scale and optional protections.
Conclusion
Security threats are faster, smarter, and harder to detect—forcing enterprises to rethink how they monitor applications and infrastructure. From logs and traces to metrics and events, the strongest security monitoring tools provide real-time visibility, reduce alert fatigue, and accelerate incident response.
CubeAPM stands out by unifying observability and security monitoring in one platform. With anomaly detection, noise reduction through smart sampling, and flat $0.15/GB pricing, it helps security teams secure apps and infrastructure without runaway costs.
As enterprises face ransomware, API exploits, and supply-chain attacks, the choice of a security monitoring tool can make the difference between a fast response and a multimillion-dollar breach. The right platform delivers more than alerts—it provides the forensic backbone to investigate, contain, and prevent threats at scale.
Disclaimer: The information in this article reflects the latest details available at the time of publication and may change as technologies and products evolve.
FAQs
1. What are the top security monitoring tools?
There are many options in the market, but most come with trade-offs like high costs or limited compliance coverage. CubeAPM stands out by offering full-stack security monitoring with transparent $0.15/GB pricing, no per-user fees, and on-prem deployment for compliance.
2. How do security monitoring tools differ from SIEM solutions?
Traditional SIEMs mainly collect and correlate logs, while modern security monitoring tools provide real-time anomaly detection, multi-signal visibility (logs, metrics, traces, events), and smarter sampling to reduce noise. CubeAPM combines both observability and security monitoring in one platform.
3. What features should a security monitoring tool include?
Key features to look for include real-time detection, compliance-ready hosting, OpenTelemetry support, predictable pricing, and rapid support. CubeAPM delivers all of these in a unified, easy-to-deploy stack.
4. Are security monitoring tools expensive at scale?
Many are—because they charge per host, user, or retention. That’s why CubeAPM uses flat ingestion pricing at $0.15/GB, saving teams compared to traditional SaaS vendors while still providing enterprise-grade monitoring.
5. Why is security monitoring essential?
With threats like ransomware, supply-chain attacks, and API exploits on the rise, continuous security monitoring is critical. CubeAPM ensures organizations can detect and respond in real time, while meeting strict compliance standards and keeping costs predictable.