Caddy server monitoring means getting full visibility into how your web traffic, TLS, and proxy layers perform, and catching issues before they cause outages. Caddy powers around 0.3% of all known websites, with Nginx still dominating ~33.3% share.
Developers and SaaS platforms choose Caddy mainly for its ease, security, and modern architecture. But when you deploy Caddy in production, you may see traffic metrics and basic logs, but hidden TLS renewal failures, slow upstream responses, or misconfigurations slip through.
CubeAPM is the best solution for Caddy Server monitoring: it ingests metrics, logs, and error traces from your Caddy instances, correlates them with upstream services, and surfaces alerts on certificate expiry, high error rates, or latency anomalies. Its MELT (Metrics, Events, Logs, Traces) coverage ensures you’re not blind to any layer of your stack.
In this article, we’re going to cover what a Caddy Server is, why monitoring Caddy Server is important, key metrics to watch, and how CubeAPM provides powerful Caddy Server monitoring.
What is a Caddy Server?
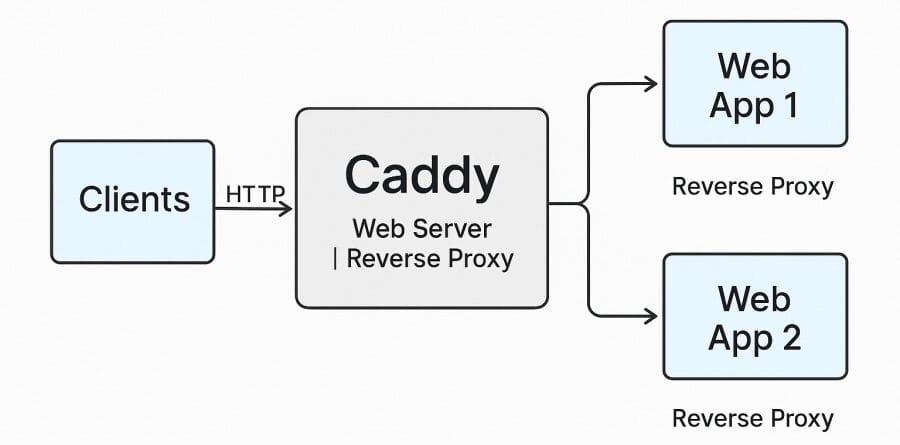
Caddy Server is a modern, open-source web server written in Go, best known for its ability to provide automatic HTTPS using Let’s Encrypt with zero configuration. Unlike traditional servers such as Apache or Nginx, Caddy focuses on simplicity and security out of the box. Its configuration can be managed through a lightweight Caddyfile or JSON, making it both developer-friendly and highly adaptable to containerized and cloud-native environments.
Caddy server monitoring is crucial because they often sit at the frontline of digital infrastructure, terminating TLS, proxying API calls, and serving user-facing applications. For businesses, the health of Caddy directly impacts uptime, customer trust, and application performance. Proactive monitoring enables teams to:
- Track TLS certificate lifecycles to avoid sudden HTTPS failures.
- Measure request and response latency to maintain fast digital experiences.
- Analyze error rates (4xx/5xx) to quickly detect misconfigurations or upstream service failures.
- Correlate logs and traces with application or Kubernetes issues to prevent outages.
By continuously observing these signals, organizations can reduce downtime, improve reliability, and ensure compliance with strict security standards.
Example: Using Caddy Server as a Kubernetes Ingress
Imagine a SaaS company deploying dozens of microservices in a Kubernetes cluster. Instead of configuring Nginx, the team opts for Caddy as the ingress controller because of its built-in TLS automation and lightweight configuration. Without monitoring in place, a failed TLS renewal could cause all services behind the ingress to become unreachable overnight. By enabling monitoring with CubeAPM, the team receives early alerts on certificate expirations, error spikes, and latency bottlenecks, allowing them to fix issues before customers ever notice.
Why Is Caddy Server Monitoring Important?
TLS automation is amazing, until renewals, OCSP, or rate limits bite
Caddy’s headline feature is automated HTTPS via ACME. Production rate limits still apply (e.g., 50 certificates per registered domain per 7 days), so bursty provisioning or misconfigured renewals can silently fail. Monitoring ACME events, renewal windows, and OCSP stapling status lets you catch problems before users see SSL errors.
Reverse proxy behavior needs visibility: upstream health, latency, and load
When Caddy fronts microservices, slow upstreams or connection-pool saturation show up as user-visible latency. Caddy’s reverse_proxy supports active (timer-based) and passive (inline) health checks; monitor their success/failure rates, timeouts, out-of-rotation backends, retries, and p95/p99 latency to separate proxy issues from app or infra issues.
Built-in dashboards are minimal, export and alert on the right metrics
Caddy exposes Prometheus metrics but doesn’t ship opinionated dashboards. Enable the metrics endpoint and scrape RPS, status-class error rates, handler durations, TLS handshakes, then alert on burn rate and SLO breaches.
Structured logs accelerate incident timelines and RCA
Caddy’s structured/JSON access and runtime logs are ideal for high-signal queries: correlate 5xx bursts to routes, upstreams, or deployments; watch log volume anomalies and route-level error leaders. Configure logging via the JSON or Caddyfile logging modules.
HTTPS is the default user expectation; breakage is immediately business-critical
Chrome’s Transparency Report shows the vast majority of page loads/time on the web occur over HTTPS, so certificate or handshake failures are instantly user-visible and revenue-impacting. Track certificate expiry, handshake failures, and OCSP stapling health as first-class signals.
Community-reported pain points are canaries; monitor them proactively
Real-world incidents frequently involve OCSP timeouts/stapling problems, renewal edge cases, or questions on RPS/latency instrumentation. Bake these into your dashboards and alerts to catch them before customers do.
Core Metrics & Signals to Monitor in a Caddy Server
Monitoring Caddy isn’t just about knowing if the service is running — it’s about observing the right signals that keep your TLS, proxying, and application delivery reliable. Below are the core categories every team should track, with examples specific to Caddy’s architecture and workloads.
Traffic Metrics
Caddy often acts as the gateway for HTTP traffic in microservice or SaaS deployments, so traffic visibility is critical.
- Requests per second (RPS): Helps you measure load patterns and detect sudden traffic surges that may indicate a DDoS attempt or inefficient scaling policies.
- Active connections: Monitor open TCP/HTTP connections to ensure Caddy isn’t overwhelmed by keep-alive or long-lived requests.
- Request latency: p95 and p99 latency values are particularly important, since even small increases here can translate into poor end-user experience.
TLS Metrics
TLS is Caddy’s superpower, but it’s also its biggest liability if not monitored closely.
- Certificate expiration: Automatic HTTPS can fail silently if renewal processes break. Proactive alerts should trigger when certificates are within 7–14 days of expiry.
- Handshake failures: High rates of TLS handshake failures may indicate cipher mismatches, expired certs, or DoS attempts.
- Auto-renewal success: Watch renewal logs and ACME events to ensure Caddy is regularly updating certificates from Let’s Encrypt without interruption.
Error Metrics
Errors are often the first sign of cascading failures in distributed systems.
- 4xx/5xx rates: Track status-class breakdowns (e.g., spikes in 502/503 errors) to detect proxy or upstream service issues.
- Failed upstream connections: Monitor retry counts and backend failures in Caddy’s
reverse_proxyto catch downstream outages early. - Response size anomalies: Unusually large or small response bodies could indicate misconfigurations, partial responses, or even security threats.
Resource Usage
Caddy’s performance depends not only on HTTP but also on underlying system resources.
- CPU usage: High CPU utilization may indicate inefficient middleware, complex TLS handshakes, or unoptimized request routing.
- Memory consumption: Essential for large-scale reverse proxy setups; memory leaks or excessive buffering can bring down the server.
- Disk I/O: If logs are written locally or caching modules are enabled, disk pressure must be tracked to prevent bottlenecks.
Custom Logs & Traces
Caddy generates structured, strongly-typed logs that are highly valuable when combined with tracing.
- Access logs: Track request paths, response codes, and latency by route to identify hotspots.
- Structured error logs: Caddy logs provide contextual JSON output — filter by module, severity, or route to speed up root cause analysis.
- Request flow tracing: Export traces (via OpenTelemetry) from Caddy’s proxy to visualize request paths across upstream services, invaluable in debugging microservice chains.
Steps to Monitoring Caddy Servers with CubeAPM
Step 1: Install CubeAPM Agent
The first step is to deploy the CubeAPM agent into your environment. For Kubernetes users, the recommended method is a Helm installation, which simplifies deploying the agent as a DaemonSet and a Deployment. Helm ensures that metrics, logs, and traces can be collected from all nodes in your cluster. If you’re running workloads inside Kubernetes, you can follow the Kubernetes installation guide for cluster-native deployment.
Step 2: Configure OpenTelemetry Collector for Caddy Logs & Metrics
Once the agent is installed, configure the OpenTelemetry Collector to ingest Caddy’s Prometheus metrics and structured logs. This requires enabling Caddy’s /metrics endpoint and pointing the Collector to scrape it. For logs, configure the OTEL filelog receiver to parse Caddy’s structured JSON access and error logs, as explained in the CubeAPM logs configuration guide. If you need tracing and span ingestion, you can extend the pipeline using the OpenTelemetry integration docs.
Step 3: Send Traces from Caddy’s Reverse Proxy to CubeAPM
Caddy can export request traces via its OTEL integration. You can configure the tracing directive in your Caddyfile or JSON config to send spans (HTTP request flows, upstream calls, latency events) to the CubeAPM Collector. This setup is detailed in the CubeAPM instrumentation guide and the OpenTelemetry integration page.
Step 4: Verify Data in CubeAPM Dashboards
After setup, verify that CubeAPM is receiving Caddy metrics, logs, and traces. CubeAPM provides pre-built dashboards for HTTP traffic, TLS certificate health, error rates, and latency percentiles. From there, you can configure custom alerts such as TLS expiry thresholds or high-latency warnings using the infrastructure monitoring reference and alerting setup guide.
Real-World Example: Monitoring Caddy Servers in a SaaS Environment
A leading fintech SaaS platform in Asia built its API gateway on Caddy Server, leveraging its built-in HTTPS automation and reverse proxy features to securely handle millions of API calls every day. Caddy’s ease of use made it the default choice for their engineering team, but its reliance on automatic TLS renewals soon became a source of risk.
Challenge
The company began facing intermittent downtime during peak trading hours because certain TLS certificates failed to renew on time. These failures were linked to DNS validation errors and Let’s Encrypt rate limits, which Caddy did not surface prominently. By the time engineers were alerted, customers were already seeing SSL errors in their browsers and mobile apps — a serious trust issue for a fintech business.
Solution
By deploying CubeAPM, the SaaS team gained deep observability into Caddy’s TLS lifecycle. CubeAPM ingested certificate expiry data, handshake metrics, and renewal logs directly from Caddy and visualized them in dashboards. They configured proactive alerts that triggered if any certificate entered a 14-day expiry window without renewal or if handshake errors spiked unexpectedly. CubeAPM’s log correlation also helped pinpoint renewal failures tied to specific domains and upstream services.
Result
Within weeks of adopting CubeAPM, the fintech reduced TLS-related outages by over 90%. Instead of reacting to customer complaints, engineers were notified ahead of time and resolved issues before expiry. This not only prevented financial transaction disruptions but also restored confidence among enterprise customers who depended on the platform for secure, always-on services.
Verification Checklist for Caddy Server Monitoring with CubeAPM
Before considering your monitoring setup production-ready, it’s important to verify that CubeAPM is correctly collecting and visualizing all critical signals from Caddy Server.
Verification Checklist
Use the following checklist to validate your configuration:
- Caddy Metrics Receiver Enabled: Confirm that the OpenTelemetry Collector is scraping Caddy’s
/metricsendpoint. This ensures HTTP traffic, TLS, and handler duration metrics are flowing into CubeAPM. - Access Logs Ingested: Check that structured JSON access and error logs are being ingested into CubeAPM. These logs should be searchable by route, status code, and latency to assist with debugging.
- TLS Certificate Monitoring Active: Validate that CubeAPM is tracking certificate expiry and handshake metrics. Alerts should be configured to notify when certificates approach expiry.
- Dashboards Functional: Ensure that HTTP latency, request rates, and TLS health are visible on CubeAPM dashboards. These panels should be refreshed in real time during traffic spikes or deployments.
- Alerting Configured: Confirm that alert rules are firing correctly and integrated with your notification channels (Slack, PagerDuty, email). Run a quick test to verify team members receive timely alerts.
Example Alert Rules for Caddy Monitoring
1. High Error Rate
Trigger an alert when more than 5% of requests fail with 5xx errors over a 5-minute interval.
groups:
- name: caddy-alerts
rules:
- alert: HighErrorRate
expr: rate(http_requests_total{status=~"5.."}[5m]) > 0.05
for: 5m
labels:
severity: critical
annotations:
summary: "High error rate on Caddy server"
description: "More than 5% of requests are returning 5xx errors in the last 5 minutes."
2. TLS Certificate Expiry
Raise a warning when a certificate has less than 7 days left before expiry.
groups:
- name: caddy-alerts
rules:
- alert: TLSCertificateExpiringSoon
expr: caddy_tls_cert_expiry_seconds < 604800
for: 10m
labels:
severity: warning
annotations:
summary: "TLS certificate expiring soon"
description: "A TLS certificate managed by Caddy will expire in less than 7 days."
3. High Latency
Alert when the 95th percentile latency for requests exceeds 500ms for five consecutive minutes.
groups:
- name: caddy-alerts
rules:
- alert: HighRequestLatency
expr: histogram_quantile(0.95, rate(caddy_http_request_duration_seconds_bucket[5m])) > 0.5
for: 5m
labels:
severity: critical
annotations:
summary: "High request latency detected"
description: "p95 request latency has exceeded 500ms for more than 5 minutes."
Why Use CubeAPM for Caddy Server Monitoring
When it comes to monitoring Caddy Servers, most teams quickly realize that generic monitoring tools don’t always scale well or remain cost-effective. CubeAPM is purpose-built to address these challenges while keeping operations simple and transparent.
- Transparent pricing: CubeAPM runs on a $0.15/GB ingestion model with no surprise fees for hosts, containers, or data transfer. Competing vendors often bill by host count or charge extra for egress, making costs unpredictable as infrastructure grows.
- Smart Sampling: High RPS workloads, such as when Caddy is fronting APIs or SaaS platforms, can overwhelm traditional monitoring budgets. CubeAPM uses intelligent, context-aware sampling to retain the most important traces (e.g., slow requests, errors) while drastically reducing overhead.
- MELT Coverage: CubeAPM unifies metrics, events, logs, and traces (MELT) across Caddy and the upstream services it proxies to. This holistic view helps teams pinpoint whether an issue originates in Caddy itself, an upstream service, or the infrastructure layer.
- Flexible Deployment: Whether you prefer SaaS for simplicity or Bring-Your-Own-Cloud (BYOC) for compliance and data localization, CubeAPM supports both. It’s also fully GDPR and HIPAA-ready, ensuring observability doesn’t compromise regulatory requirements.
- Faster Debugging: With CubeAPM, teams can correlate Caddy reverse proxy errors directly with Kubernetes pod crashes, DNS misconfigurations, or upstream service failures. This reduces mean time to resolution (MTTR) and ensures incidents are resolved before they impact customers.
Conclusion
Monitoring Caddy Servers is essential for ensuring uptime, performance, and security in modern infrastructures. From TLS certificate renewals to reverse proxy health and latency tracking, the right observability strategy can mean the difference between seamless user experiences and costly downtime.
CubeAPM makes this process simple and scalable. With transparent pricing, full MELT coverage, and integrations across Kubernetes, Prometheus, and cloud services, teams gain a unified view of Caddy alongside their applications and infrastructure. This reduces blind spots and accelerates troubleshooting.
Start monitoring Caddy with CubeAPM today. Deploy in under 10 minutes, gain complete visibility into your Caddy layer, and prevent outages before they impact your customers.
Disclaimer: The information in this article reflects the latest details available at the time of publication and may change as technologies and products evolve.
FAQs
1. Can Caddy Server expose Prometheus metrics natively?
Yes. Caddy has a metrics module that exposes Prometheus-formatted metrics on the admin API (typically at /metrics). Once enabled, these metrics can be scraped by Prometheus or ingested into CubeAPM via the OpenTelemetry Collector.
2. How do I monitor Caddy Server in Kubernetes environments?
When Caddy is deployed as an ingress in Kubernetes, monitoring involves scraping the /metrics endpoint, forwarding pod logs, and tracing requests through the OpenTelemetry Collector. Tools like CubeAPM unify these signals so you can see both Caddy and upstream workloads in a single dashboard.
3. Does Caddy log structured data that’s easy to analyze?
Yes. Caddy logs are structured JSON by default, making them easier to parse and filter. This helps with building alerts (for example, filtering by status codes or request paths) and integrating logs directly into platforms like CubeAPM.
4. What TLS-specific issues should I watch out for when monitoring Caddy?
Common issues include failed ACME renewals, DNS validation errors, and TLS handshake timeouts. These don’t always surface immediately in basic health checks, which is why monitoring certificate lifecycles, expiry times, and renewal logs is critical.
5. Can I integrate Caddy monitoring with third-party tools like Grafana?
Yes. Since Caddy exposes Prometheus metrics, you can integrate them into Grafana dashboards. However, combining this with CubeAPM offers more value because it correlates Caddy metrics with logs, traces, and infrastructure events across your stack.







